Bulletin
On Tuesday, March 25, Google promptly released1 a patch for a sandbox escape vulnerability in its Chrome browser, following a mid-March publication by Kaspersky threat researchers2 about a professional hacking operation utilizing drive-by download exploits. Infoblox identified the malicious infrastructure used in this attack on February 5, merely three hours after the domain was registered. Other vendors also added this domain two weeks after the attack.
What:
- Mid-March 2025, Kaspersky technologies detected2 a wave of infections by previously unknown and highly sophisticated malware targeting hidden Google Chrome web browser vulnerability. In all cases, infection occurred immediately after the victim clicked on a link in a phishing email and visited the attackers’ website – no further action was required.
Who:
- The cyberespionage campaign, dubbed Operation ForumTroll3, targets Russian organizations, including media outlets, educational institutions, and government agencies.
- Attackers sent personalized phishing emails with a malicious link. According to Kaspersky’s researchers, the email phishing lures were disguised as invitations from a scientific forum called “Primakov Readings” and were designed to trick victims into downloading additional malicious code.
- The initial exploit was designed to escape Chrome’s sandbox and work with another exploit that enables remote code execution.
Impact:
- As advanced exploits are often sold on underground forums, other financially motivated actors may adopt these exploits, resulting in further proliferation.
Infoblox Detection:
- The malicious domain, primakovreadings[.]info, used in this attack was discovered by Infoblox Threat Intel and blocked by Infoblox Threat Defense™ on February 5, just three hours after the domain was registered.
- By using unique DNS telemetry and advanced data science, Infoblox Threat Intel provided an early detection advantage of 43 days before the first threat research was publicized. Infoblox also flagged this domain as “high-risk” allowing defenders to automatically block access before the phishing attack.
| Publicly Reported Domain | Threat Research Publication Date | Infoblox Discovery | Early Protection Metric |
|---|---|---|---|
| primakovreadings[.]info | 3/20/25 | 2/5/25 | 43 days |
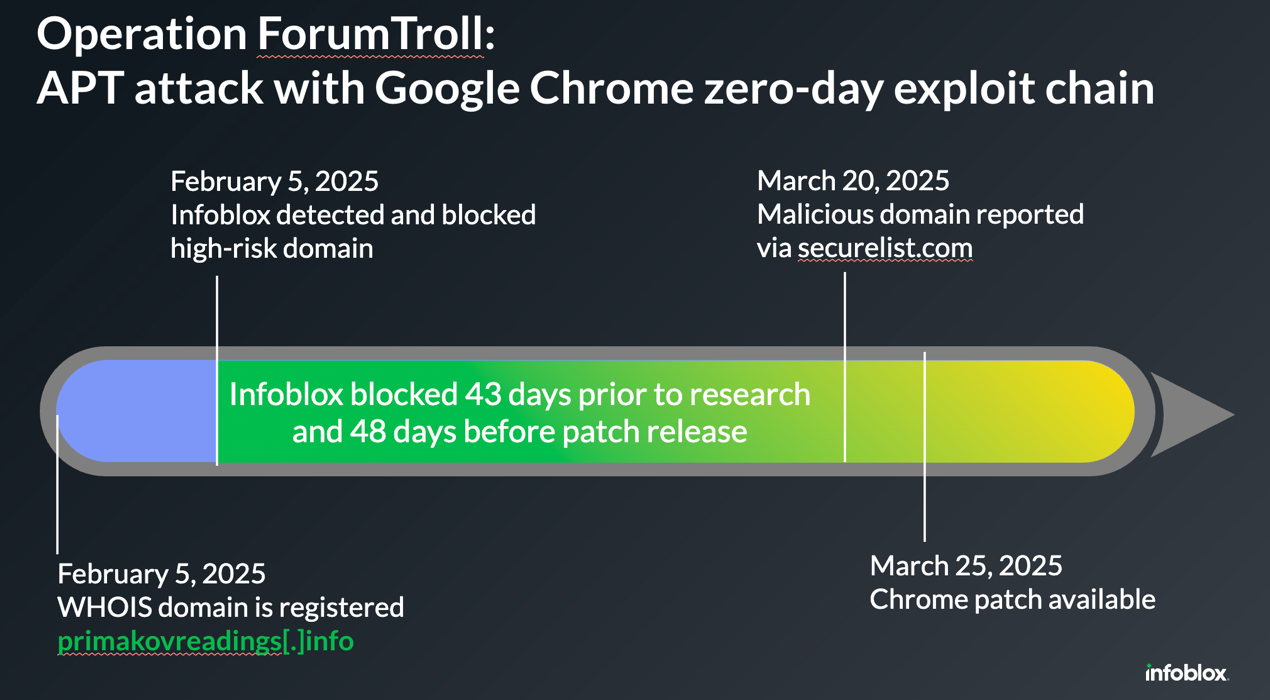
Picture 1: Timeline overview from domain registration to vulnerability patch fix.
Infoblox Protection and Recommendations :
- Infoblox customers running in blocking mode using high-risk feeds were protected from this dangerous domain.
- Infoblox DNS-based protection offered the first shield against the sophisticated zero-day attack covered under CVE 2025-2783, 48 days ahead of the patch release.
Recommended Action:
Request a security workshop to learn more about early detection using DNS
Learn more about Infoblox Threat Intel and Infoblox Threat Defense
Footnotes
- https://chromereleases.googleblog.com/2025/03/stable-channel-update-for-desktop_25.html
- https://www.kaspersky.com/blog/forum-troll-apt-with-zero-day-vulnerability/53215/
- https://securelist.com/operation-forumtroll/115989/








