What Does the CDC Have to Do with the English Premier League?
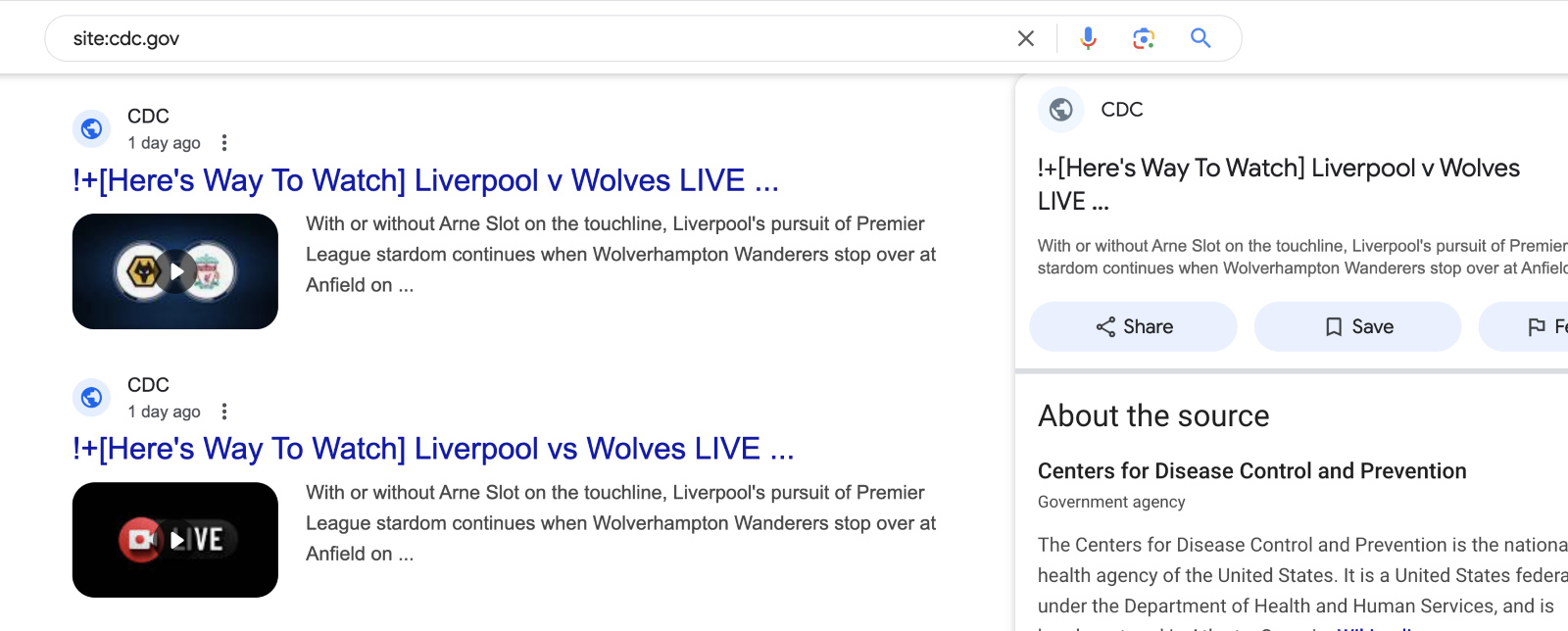
Picture 1: Search results for English Premier League soccer game
If you’re a fan of English Premier League soccer and didn’t have an easy way to watch the Liverpool-Wolverhampton match on February 16, you may have run across the ads above. And the more observant among you may have wondered, “Why is the U.S. Center for Disease Control and Prevention (CDC) providing helpful hints on watching the match live?”
The short answer is that they weren’t. The links above took you into a morass of malware and malicious content, including scam, scareware and fake dating sites. But why would the CDC—the United States’national public health agency—do such a thing? Surely their remit hasn’t changed that much!
Of course it hasn’t. But maybe the best question—and the one nearest and dearest to our hearts—is what this all has to do with DNS.
That’s what we’ll look at in this article: how threat actors were able to capitalize on poor DNS hygiene by the CDC to make malicious content available under the auspices of a trusted organization.
A Primer on Embedded CDN Content
First, we need to look at how content from content delivery networks (CDNs) is accessed—for example, how it’s embedded in websites. Most big websites load lots of content from CDNs: It’s how everything from graphics and videos to annoying ads are delivered quickly and efficiently to your browser.
A common way to embed CDN content is to refer to it by a domain name in your namespace, which is an alias for a domain name in the CDN’s namespace.
A DNS lookup for ahbazuretestapp.cdc.gov may give the below results:
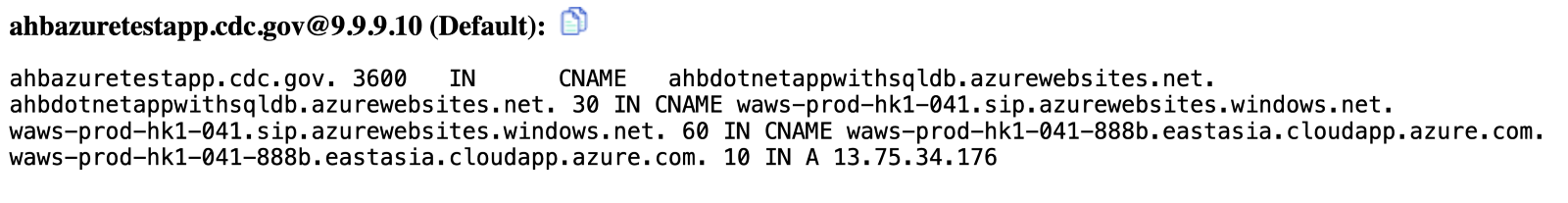
Picture 2: DNS lookup for ahbazuretestapp.cdc.gov
It’s a good guess that the domain name ahbazuretestapp.cdc.gov represents a CDC Azure test app of some kind.
- The first CNAME record creates an alias from ahbazuretestapp.cdc.gov (a domain name in the CDC’s cdc.gov namespace) to a domain name in Microsoft’s azurewebsites.net domain. (Picture 3: Normal Situation)
- That, in turn, is an alias for another domain name in Microsoft’s windows.net domain, which is yet another alias for a domain name in azure.com. (All the aliases after the CDC’s support advanced load distribution; virtually all CDNs use a system like this.)
The Dangers of Poor DNS Hygiene
This is all well and good. Now let’s say the CDC decommissions their Azure test app and stops paying Microsoft to host it (Picture 3: Decommissioning). Microsoft then removes the second CNAME record, linking the target of the old CDC alias to their CDN infrastructure. But the CDC neglects to delete the old ahbazuretestapp.cdc.gov CNAME record.
A malicious actor can now use their account with the same CDN (Picture 3: Actor steps in) to create new content that uses the same domain name as the target of the CDC’s alias, ahbdotnetappwithsqldb.azurewebsites.net, thereby gaining control of the content that the CDC’s alias points to.
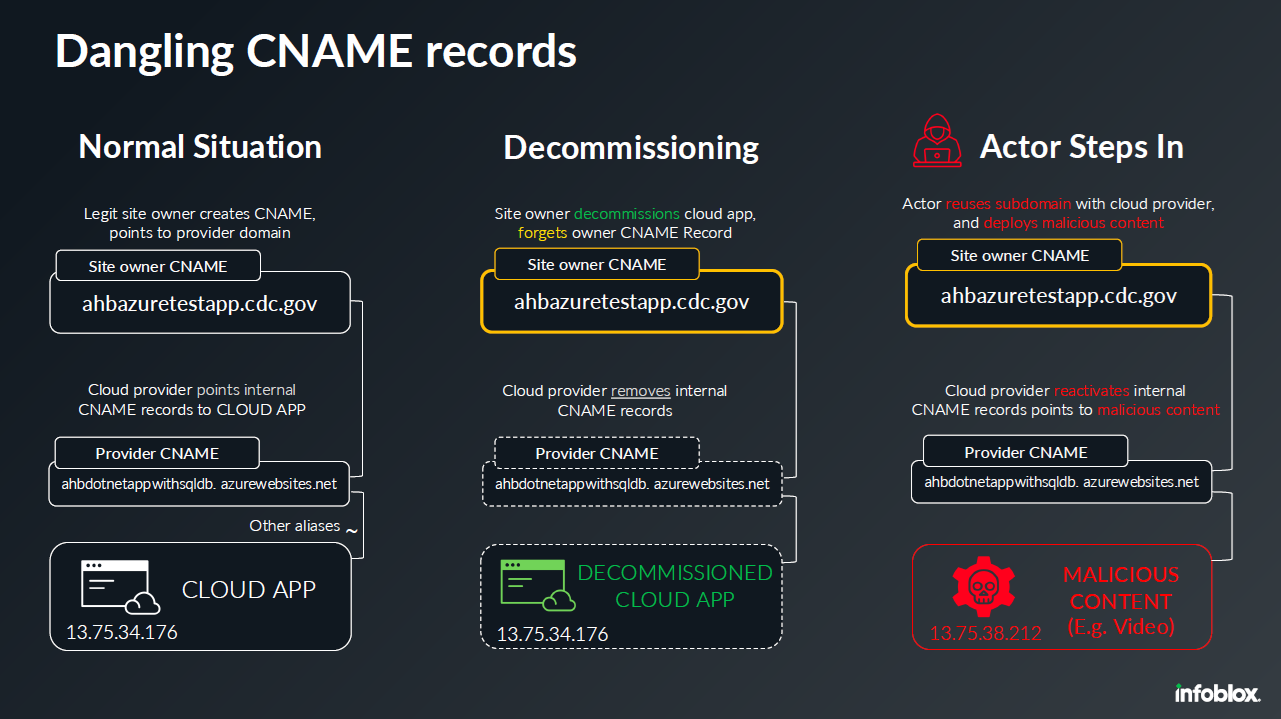
Picture 3: Dangling CNAME Records: How actors abuse legit domains.
But wait—this may not seem like a real security risk. After all, the CDC has presumably removed references to the Azure test app from their websites (or wherever). There’s no way for an unassuming user to reach the malicious content!
Indeed, but there is: Google and other search engines can still search and index the content and add it to their results (4). And that’s exactly what those Liverpool and Wolverhampton fans saw.
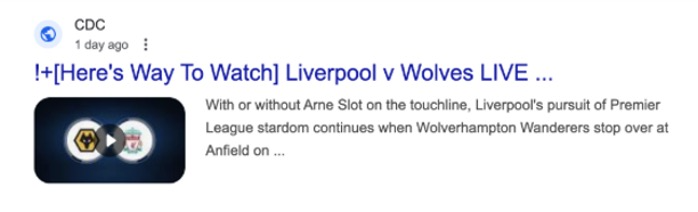
Picture 4: Malicious content with high reputation CDC domain found by search engine.
Why would our malicious actor bother? Because they want to capitalize on the reputation of the CDC. Results from an authoritative source like the CDC will naturally percolate to the top of a search engine’s results. That means users are much more likely to access the malicious advertisements, and that much more likely to believe it’s genuine. Our malicious actor is trading off the CDC’s good name.
There are several other ways for a malicious actor to abuse his control of the CDC’s domain name. They could:
- Distribute malware from what appears to be the CDC
- Harvest the contents of web cookies for *.cdc.gov
- Get an SSL certificate for the domain name and gain access to secure cookies for *.cdc.gov
- Mount a phishing campaign from email addresses using the domain name
Who Is Our Malicious Actor?
It’s natural to wonder who our malicious actor is. Clearly, it’s someone—or some organization—clever enough to identify dangling CNAME records and to know how to exploit them.
We visited many URLs that used these compromised domain names. Most led to malicious content delivered through a traffic distribution system (TDS) hiding the malicious advertiser’s identity. We were asked to click “Allow” to watch a video, but instead of showing the video, we were redirected to a scam website offering scareware or a fake dating service, or in some cases distributing malware.
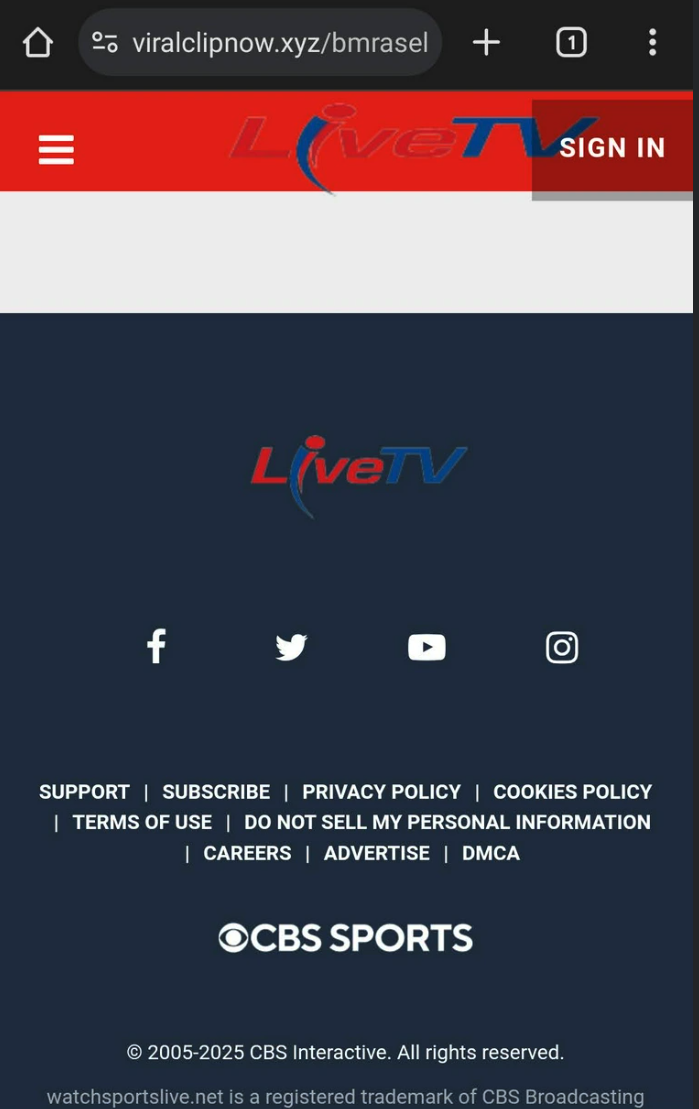
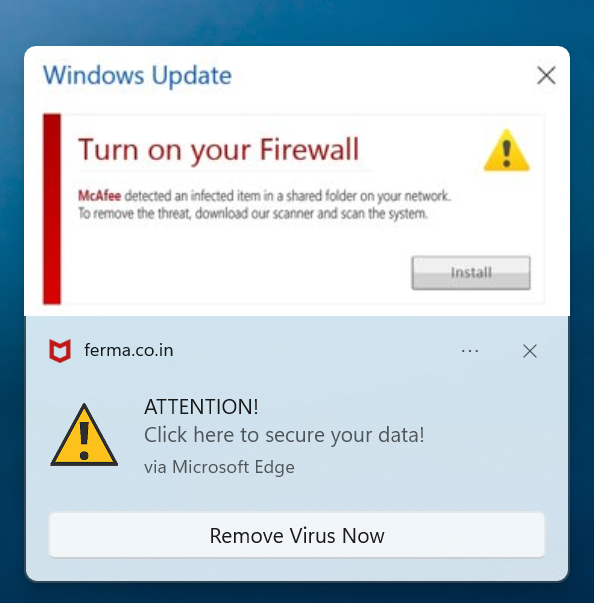
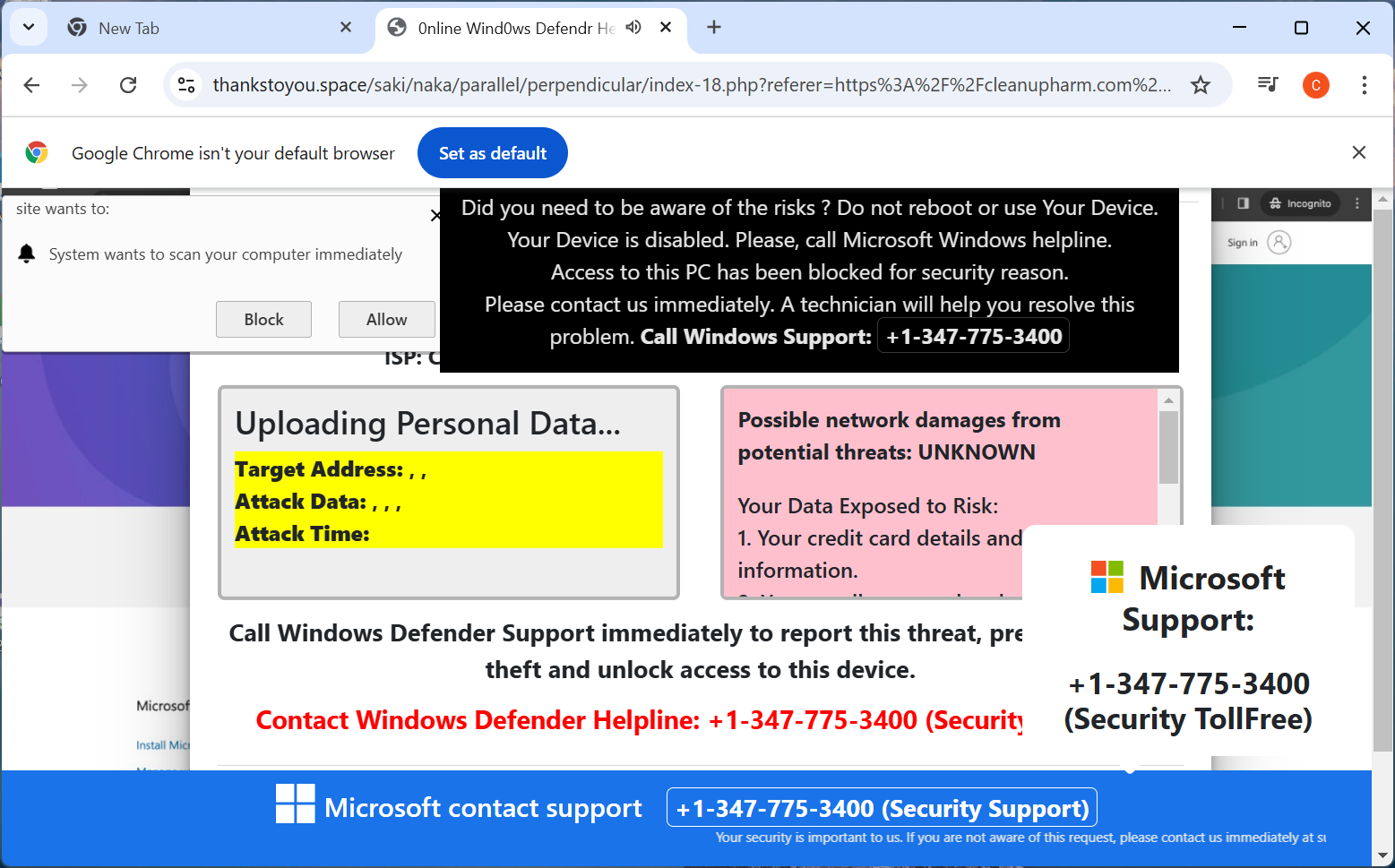
Picture 5: Malicious content presented by the actor
The TDS appears to be a Russian actor that advertises on the Dark Web. Not much is known about them. Interestingly, the malicious actor also seems to use Sitting Ducks attacks, which we’ve previously covered.
Protecting Yourself
The best way to safeguard against having your namespace fall victim to this vulnerability is to clean up those old CNAME records.1 Deleting unused CNAME records eliminates the possibility of someone assuming control of the targets of those CNAME records and masquerading as your organization.
Many of these unused CNAME records are dangling—that is, they point to nonexistent domain names, at least until our malicious actor notices them and commandeers the target domain names for themselves. Fortunately, identifying dangling CNAME records is relatively straightforward:
- use Infoblox Universal Asset Insights™ to gain comprehensive DNS visibility and insights across hybrid and multi-cloud environments.
- use a Microsoft script (found here) to find dangling records.
Equally important is preventing your users from visiting these compromised domain names. Since the malicious actors point these domain names to TDSs, Protective DNS is an ideal mechanism for blocking them. Infoblox provides threat feeds that enable your DNS infrastructure to block the resolution of domain names through TDSs and Infoblox Threat Defense™ blocks their resolution in the cloud.
To learn more about Infoblox Threat Intelligence Research visit https://www.infoblox.com/threat-intel/.
Request DNS Security Workshop
https://info.infoblox.com/sec-ensecurityworkshop-20240901-registration.html
Footnotes
- We feel a little presumptuous telling the CDC how to protect themselves after relying so much on them for advice over the years, but this is DNS, not infectious disease.











