Cybercriminals jumped at the opportunity last week to use the U.S. presidential debate as fodder for a new cryptocurrency scam. Victims were lured by deep fake videos claiming to show Elon Musk joining Donald Trump in a “fiery” debate against Kamala Harris. Unfortunately for viewers who tuned in to see Musk and Trump team up against Harris, the streamed session started with Musk saying that Trump could not join him because he is occupied with the Harris debate. After that, the video turns to the theme of cryptocurrency and tells viewers that they could win big by investing in cryptocurrency during the streamed event.
Infoblox first reported this campaign in a Mastodon post shortly after it began. The videos were streamed from well-established YouTube accounts, some with over 2.4M subscribers, and at one point on Saturday, we saw over 184k accounts watching one of the videos live. The videos contained QR codes linked to domains that are made to look like the candidates or cryptocurrency platforms, adding further deception. All of this demonstrates how criminals take advantage of high-profile current events, social media, and artificial intelligence (AI) to make money. While YouTube took down account after account, some videos were available for over 12 hours, tricking an untold number of users. But by blocking access to suspicious domains, users can be protected from these clever scams.
While Infoblox and other researchers from Guardio and BitDefender have reported on the use of hijacked YouTube channels to advertise crypto-currency scams in the past, this campaign differs in that the actors behind it attempt to leverage current events, namely the presidential debate, to get their videos close to the top of search results. In January 2024, BitDefender was one of the first to report on the use of deep fake technology to alter existing videos to include content that promotes the scams and to add legitimacy, but the content was not related to a specific event. As press around the debate faded, these actors took advantage of the news cycle with videos this week entitled “Elon Musk Reveals Insights on Trump Assassination Attempt and Election Support.” This video was also quickly taken down, but we captured a copy; view it here.
Stream-jacking YouTube Channels
The scam starts with a hijacked YouTube channel using a process referred to as “stream-jacking.” Cybercriminals choose victim channels based on the number of subscribers and views: channels that have high traffic so that their content will get the widest distribution possible before being taken down. In this campaign, once the victim channel has been hijacked, it is slowly transformed into a (fake) Tesla-branded channel. This includes changing the name and imagery of the channel and uploading numerous official Tesla videos (see Figure 1).
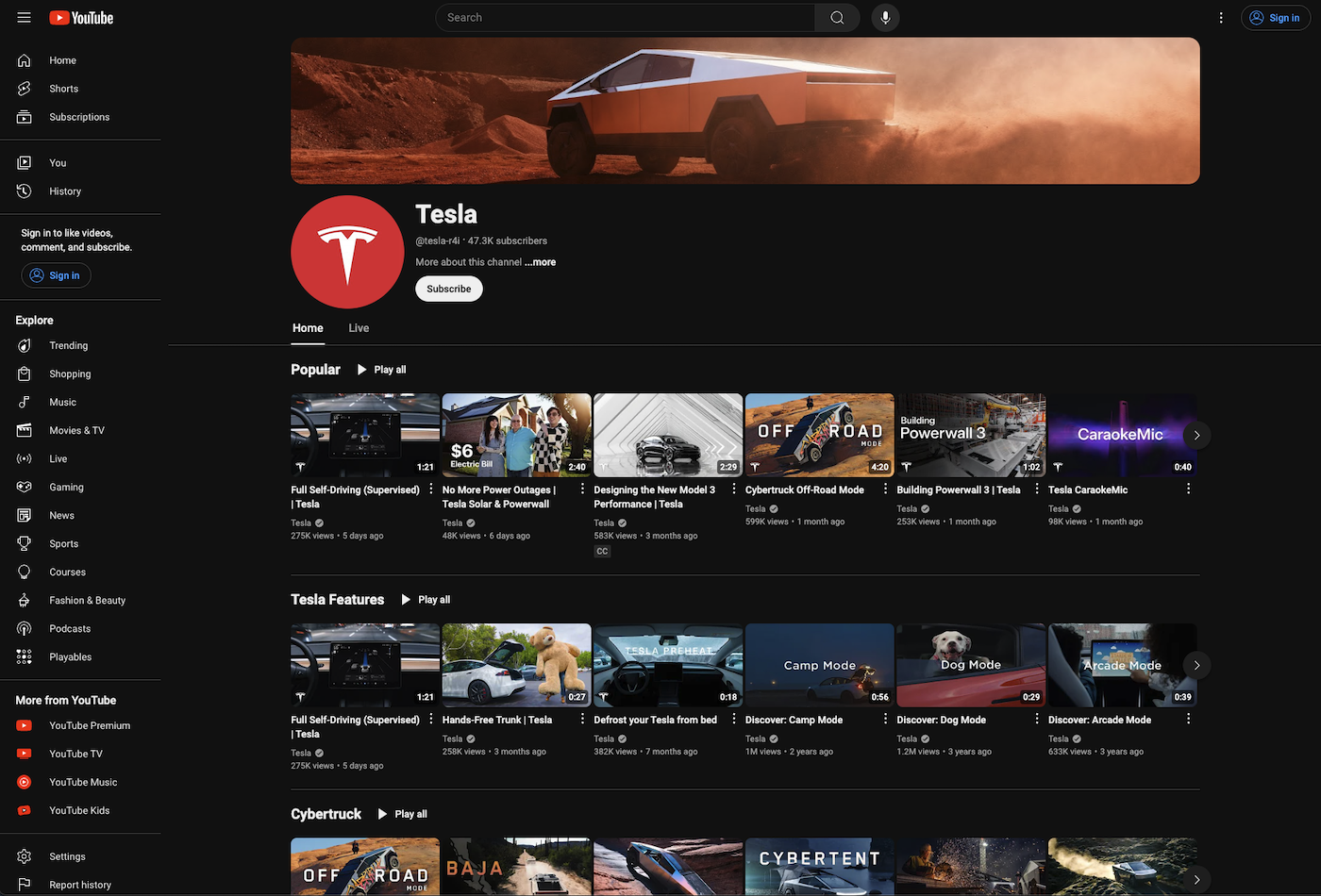
Figure 1: The (fake) Tesla-branded YouTube channel https://www.youtube[.]com/@tesla-r4i which hosts Tesla videos
Once the re-branding of the channel is complete, the malicious content is added as a “livestream” to the channel (see Figures 2 and 3). However, the videos are not actually live at all. They are simply pre-recorded videos played on a loop with text overlays suggesting it is live. The “livestream” is repeated across multiple stream-jacked channels simultaneously and can be found using a simple search (see Figure 4). One of the streams indicated there were 184k viewers watching it. We suspect that threat actors used bot traffic to inflate the view counts to make the videos and the crypto event seem more legitimate.
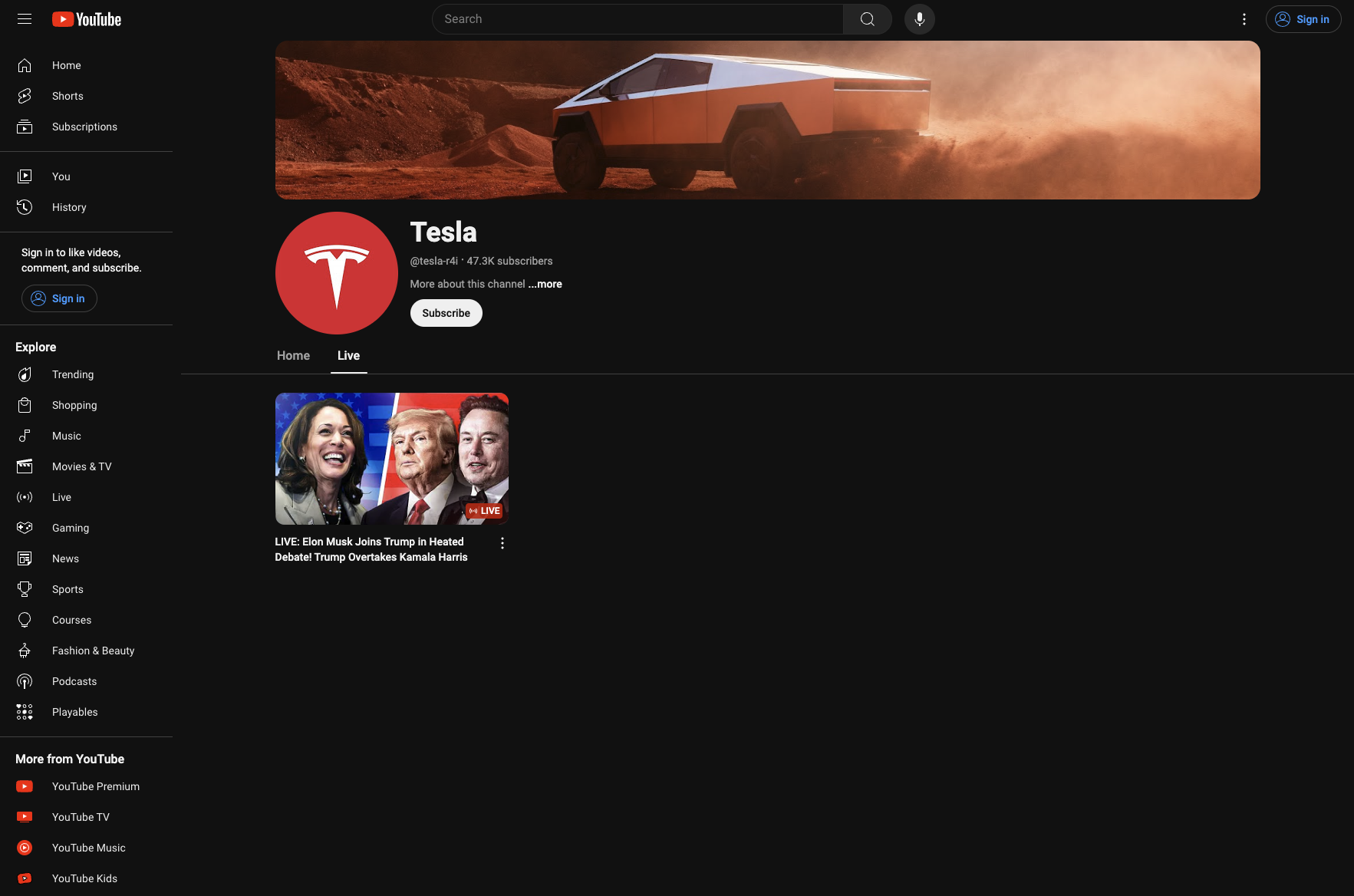
Figure 2: The “live” stream video using a Trump-Harris debate theme on the same YouTube channel
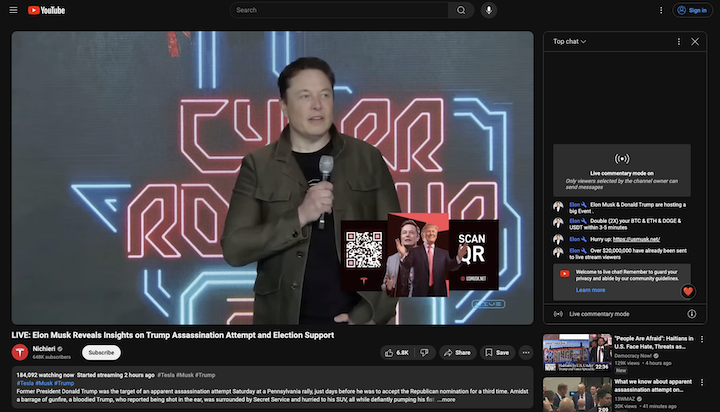
Figure 3: A screenshot of the “live” YouTube stream using deep fake Elon Musk audio seen on multiple fake Tesla YouTube channels and hijacked legitimate channels
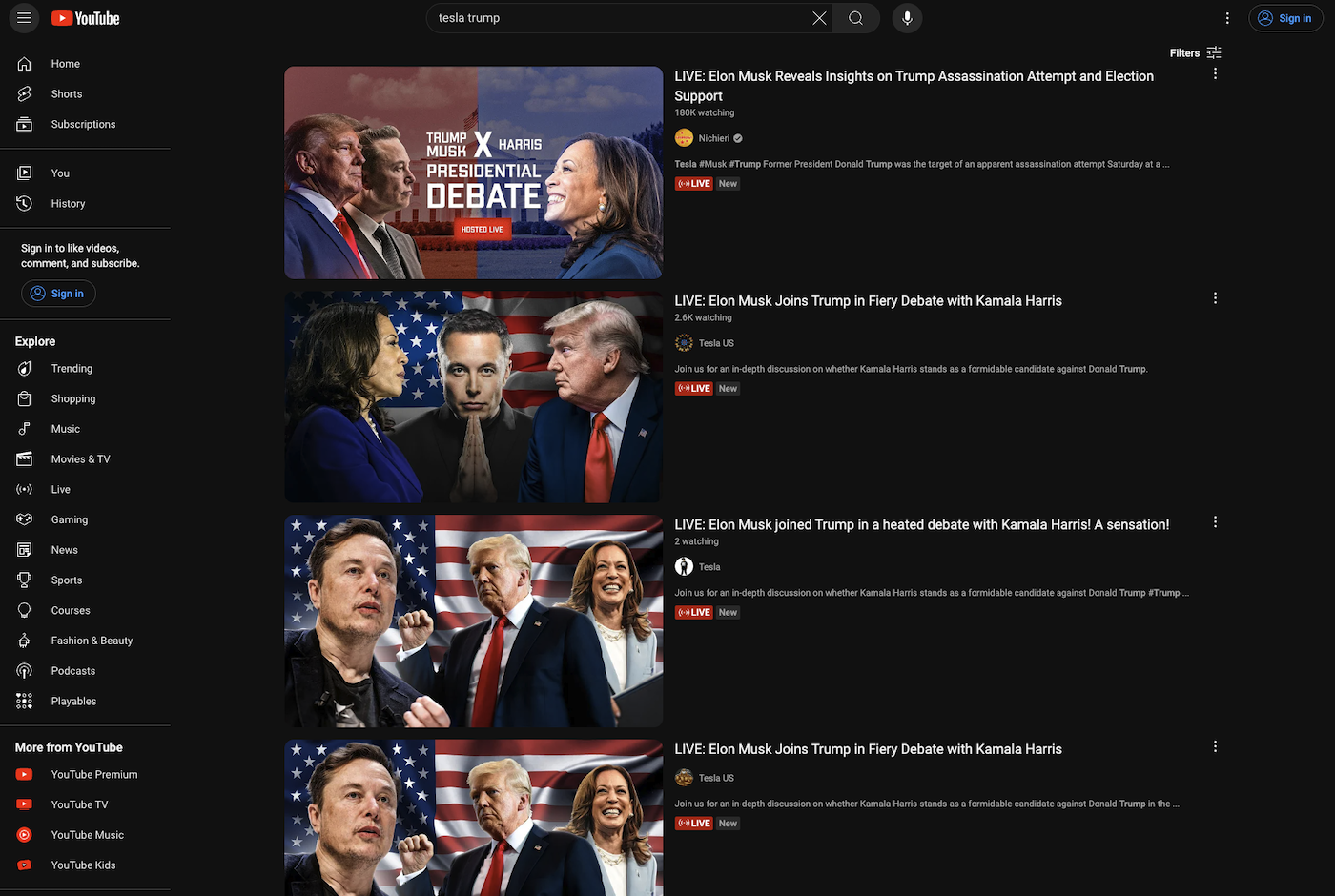
Figure 4: Search results for livestreams using the keywords “tesla” and “trump”
Scam Domains
The livestream video prominently displays a QR code that links to the site hosting the crypto scam. The scam sites use domain names that are lookalikes to cryptocurrency sites, Tesla, and the debate, e.g., trump-debate[.]com. The domains found in this campaign all have some Russian nexus, including the use of a Russian registrar or hosting provider. While the debate-specific domains were recently registered, the cryptocurrency lookalike domains were registered some time ago, including eth23[.]io and chaindrop[.]promo.
The scam sites in this campaign use Cloudflare anti-bot landing pages to prohibit web scraping from crawlers operated by security researchers, from seeing the content of the sites. Once the anti-bot landing page has been bypassed and the page is loaded, potential victims see a page like that in Figure 5, wherein the subjects in the videos change from campaign to campaign. Victims are urged to link their crypto wallet to be eligible to win a prize. While the branding and content of the sites are fake, there is some real information on the site. In the presidential debate-themed campaign, victims are asked to send funds to the displayed crypto wallet addresses, which belong to the cybercriminals. In many other campaigns, the crypto wallet addresses are found hidden in JavaScript. Following the QR codes in the debate-themed livestreams, we were able to find the crypto wallet addresses shown in Table 1, one of which has gathered over $4,000 in Dogecoin transactions (see Figure 6).
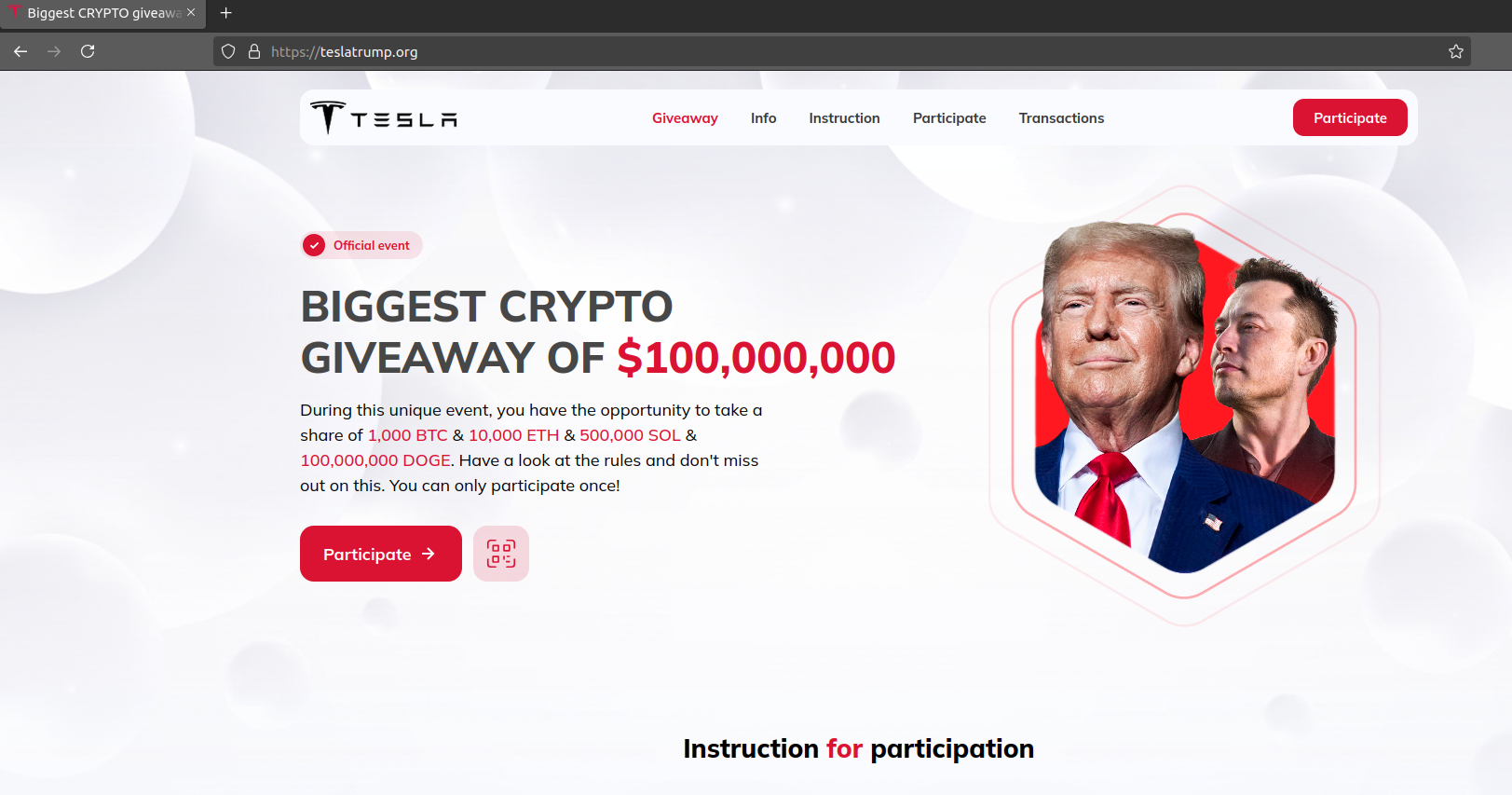
Figure 5: The content of one of the crypto scam sites advertised in the livestream videos using a QR code
| Wallet address | Type |
|---|---|
| bc1qfwjgvwesz5k2dpjpvwueze2v009wjh76hn9gfn | Bitcoin |
| bc1qjanjaawj4g0n5xlm03dmpx97u5yrpzljuhuxz8 | Bitcoin |
| 6XxsCPnWBY4ciWhEN5P9GiTWxuDHwomQkDsHJNC7hrTf | Solana |
| 8iwdRkeBDr6RzpkvkcMzqAFqr9L9eGKCKzHHZdzB6MQx | Solana |
| 0x70c774951b96Cb7EcA192505da81CEAddf6F3C92 | Ethereum |
| 0xD7C3F7dC1Dfa6F64F778ddfC9Ea1a4d2dA2131b4 | Ethereum |
| D6ShMStqVGWwgHPAZZkw9UK49oP4JZJAz4 | Dogecoin |
| DKV1nsGp6DYVZ4fze8zYJbPti9MbGcXGWB | Dogecoin |
| Table 1: Cryptocurrency wallet addresses owned by the threat actor and used in the Trump-Harris presidential themed scam campaigns | |
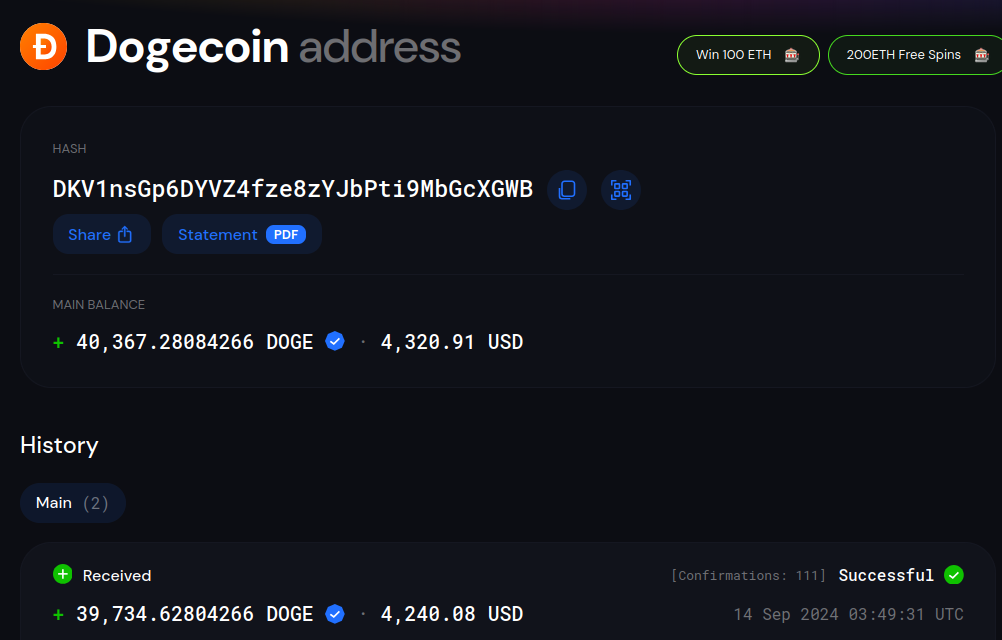
Figure 6: One of the crypto wallets used in the debate-themed scam showing over $4,200 USD in Dogecoin transactions
Prevention and Mitigation
As cybercriminals employ new techniques and technologies such as deep fakes, the lures become more believable and the need for proactive defense becomes more important. Infoblox Threat Intel has numerous algorithms to identify suspicious and lookalike domains as they are registered or configured by cybercriminals. By leveraging DNS to protect their networks, BloxOne Threat Defense customers are protected from these and a multitude of other threats. With over 15M domains in our suspicious and malicious blocklists, the percentage of false positives reported remains below 0.0002%, giving enterprises and end users confidence that they are protected regardless of how the domain is used.
IoAs
The table below provides IoAs (indicators of activity) used in this campaign; for more, go to the Infoblox Threat Intelligence Github repo: https://github.com/infobloxopen/threat-intelligence/tree/main.
| Indicator | Type | Note |
|---|---|---|
| https://www.youtube[.]com/@tesla.trump.debate | YouTube channel | Potentially hijacked YouTube channel |
| https://www.youtube[.]com/@Tesla.lives.2444 | YouTube channel | Potentially hijacked YouTube channel |
| https://www.youtube[.]com/@Tesla-i5g/streams | YouTube channel | Potentially hijacked YouTube channel |
| https://www.youtube[.]com/@polaris.spacex.24.7 | YouTube channel | Potentially hijacked YouTube channel |
| https://www.youtube[.]com/@tesla-e1u/streams | YouTube channel | Potentially hijacked YouTube channel |
| https://www.youtube[.]com/@tesla-k4k | YouTube channel | Potentially hijacked YouTube channel |
| https://www.youtube[.]com/@tesla-r4i | YouTube channel | Potentially hijacked YouTube channel |
| https://www.youtube[.]com/@lives.micro.corp24 | YouTube channel | Potentially hijacked YouTube channel |
| debate[.]gift | Domain | Crypto scam site |
| tesladebate[.]com | Domain | Crypto scam site |
| teslatrump[.]org | Domain | Crypto scam site |
| trump-debate[.]com | Domain | Crypto scam site |
| trumptesla[.]org | Domain | Crypto scam site |
| trump-elon[.]gives | Domain | Crypto scam site |
| usmusk[.]net | Domain | Crypto scam site |
| promo-tesla[.]io | Domain | Crypto scam site |
| ark-fund[.]pro | Domain | Crypto scam site (old) |
| chaindrop[.]promo | Domain | Crypto scam site (old) |
| crypto-participate[.]com | Domain | Crypto scam site (old) |
| doubleetherx2[.]com | Domain | Crypto scam site (old) |
| eth-up[.]gift | Domain | Crypto scam site (old) |
| eth23[.]io | Domain | Crypto scam site (old) |
| ether2022[.]info | Domain | Crypto scam site (old) |
| eththemerge[.]net | Domain | Crypto scam site (old) |
| eththemerge[.]survay[.]pro | Domain | Crypto scam site (old) |
| give-toncoin[.]com | Domain | Crypto scam site (old) |
| harryteams[.]com | Domain | Crypto scam site (old) |
| takeeth[.]net | Domain | Crypto scam site (old) |
| x2-event[.]pro | Domain | Crypto scam site (old) |
| x2coinbase[.]org | Domain | Crypto scam site (old) |








