Bulletin
Who:
- Starting in early March 2024, Rapid7 identified the distribution of malicious trojanized installers for the open-source utilities WinSCP and PuTTY. These installers are being spread through malicious ads on popular search engines, which direct users to typo-squatted (lookalike) domains. In at least one instance, this led to an attempted ransomware deployment. Rapid7’s updated analysis includes new indicators of compromise, a YARA rule for detecting malicious DLLs, and changes in the malware’s functionality. The threat actor(s) behind this campaign remain unknown.
What:
- This campaign primarily targets IT team members, who are more likely to download the trojanized files while searching for legitimate versions. Once executed, the malware grants the threat actor elevated access and complicates analysis by obscuring subsequent administrative actions.
- WinSCP is a file transfer client, and PuTTY is a secure shell (SSH) client. The infection chain typically starts when a user searches for terms like “download WinSCP” or “download PuTTY” on a search engine such as Bing. The search results include an ad that redirects the user to a clone of the legitimate website (for WinSCP) or a simple download page (for PuTTY). Both pages contain a link to download a zip archive with the trojan from a secondary domain.
Infoblox Capability:
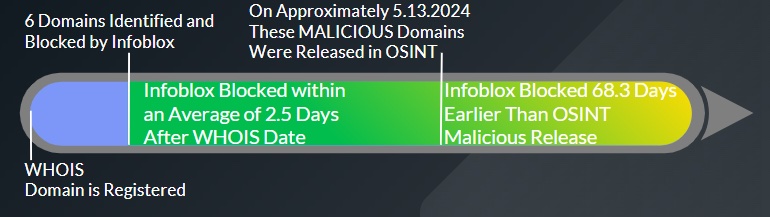
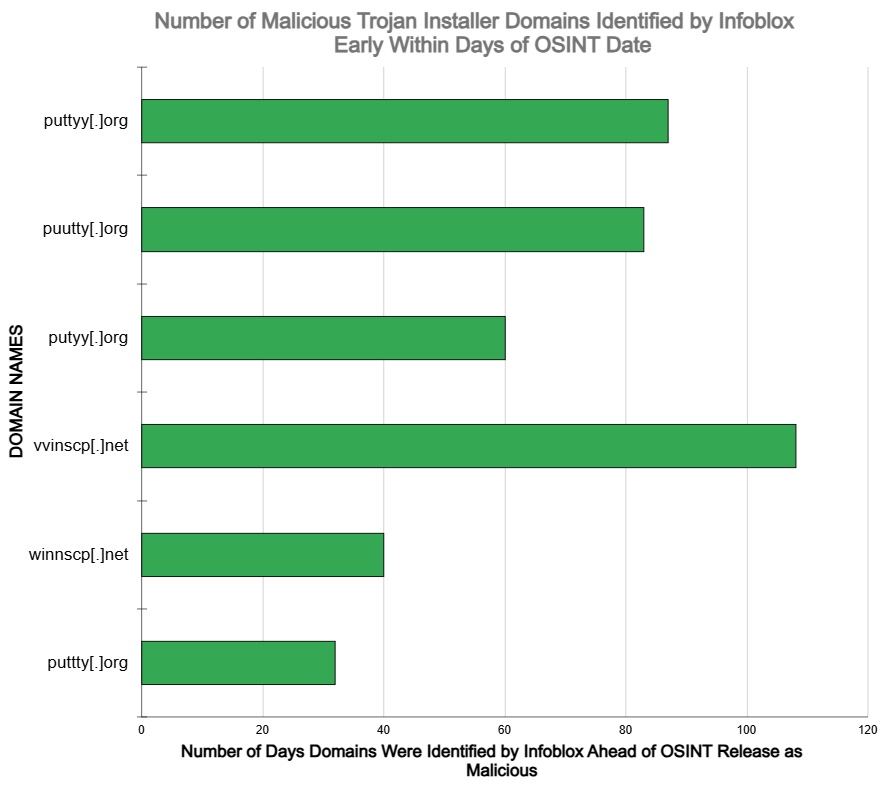
- Infoblox DNS Early Detection identified key Malicious Trojan Installer Domains for WINSCP and PUTTY shortly after registration and days to months ahead of availability in OSINT as MALICIOUS.
- Infoblox identified and blocked 6 MALICIOUS domains—60% of the Malicious Trojan Installer Domains for WINSCP and PUTTY —an average of 68.3 days earlier than OSINT availability.
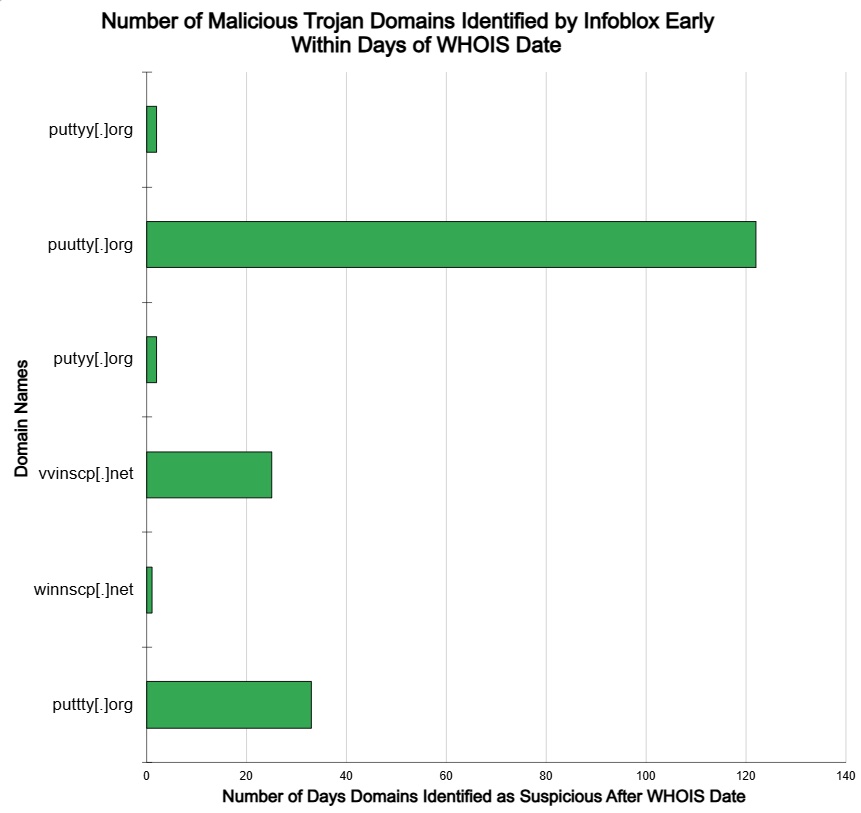
- Similarly, Infoblox identified and blocked the same 6 Malicious Trojan Installer Domains for WINSCP and PUTTY within an average of 2.5 days of their WHOIS registration. More than half were blocked in 1 to 3 days of the WHOIS registration. One domain was identified as a Zero Day DNS and identified on the same date as the WHOIS registration.
- Malicious Trojan Installer Domains for WINSCP and PUTTY:
| MALICIOUS DOMAIN | INFOBLOX IDENTIFICATION |
|---|---|
| puttyy[.]org | – phishing Lookalike |
| puutty[.]org | – phishing Lookalike – Zero Day DNS |
| putyy[.]org | – suspicious Nameserver |
| vvinscp[.]net | – suspicious Nameserver |
| winnscp[.]net | – phishing Lookalike |
| puttty[.]org | – phishing Lookalike |
Infoblox Impact:
- Infoblox customers running in blocking mode using our high-risk feeds were protected from the campaign.
- Our feeds could be used to automatically block these malicious domains, which resulted in breaking the threat actor’s Kill Chains wherever they were found.
- Infoblox Threat Intel is HIGH VALUE, can be used with relatively LOW EFFORT, and can SHRINK THE TIME TO VALUE and INCREASE THE RETURN ON INVESTMENT for your threat intelligence program.
Recommended Action:
Click here to be connected with Infoblox to assess your security posture.
Analysis And Methodology:
Infoblox then extracted malicious domains identified within the Rapid7 blog and other sources. The Infoblox team then analyzed the malicious domains identified earlier by our feeds to determine if they were identified earlier.
We used our lookalike domain technology to identify domains earlier than OSINT availability in four instances. A lookalike domain is designed to resemble a legitimate domain, often used in cyberattacks. Cybercriminals create these malicious domains to deceive users into thinking they are interacting with a trusted entity. This can lead to phishing, malvertising, and other similar attacks.
| Infoblox identified 60% of the Malicious Trojan Installers for WINSCP and PUTTY domains an average of 68.3 days earlier than OSINT availability. This enabled our customers to stop the execution of the intended Cyber Kill Chain1 by automatically blocking access to these dangerous domains. |
Our team researched each malicious domain identified in OSINT in the Infoblox Dossier portal. We reviewed our timeline feature to extract the earliest dates associated with Infoblox’s high-risk designation. We also extracted the WHOIS information for additional context.
Our early identification of these domains has provided compelling timeline data. Our team found that, in many cases, the threat actors were already ramping up activity shortly after we included them in our feeds and long before visibility to the public at large via OSINT availability.
| It is normal that the dangerous domains in our data cloud are queried and blocked within days to a few weeks after we include them in our feeds. Threat actors are generally active and successful many months before the availability of OSINT information unless you were using Infoblox Threat Intel feeds. |
The conclusions of our analysis illustrate the potential benefits of Infoblox Threat Intel feeds:
- 6 of the Malicious Trojan Installers for WINSCP and PUTTY domains were identified as high risk by Infoblox an average of 68.3 days (2.25 months) before the OSINT designation as malicious became available. This same group of domains was identified within an average of 2.5 days after the WHOIS domain registration date.
- One of the identified domains, puutty[.]org was identified as a phishing lookalike – Zero Day DNS. Infoblox detected this and blocked it on the same day as the WHOIS date.
- Our DNS early detection program identifies high-risk domains weeks to months ahead of OSINT’s identification as malicious.
OSINT publication dates may sometimes be unclear or lack precision. The dates of published articles by reputable 3rd parties may not always accurately reflect the OSINT availability of each domain. The critical point is that even if you have the OSINT data, it must propagate through the threat feeds you use and your cybersecurity ecosystem to support actionable policies. This is all automated with Infoblox DNS Detection and Response (DNSDR) and our threat intel data.
Comparison To Whois Data
WHOIS data draws a line in the sand and gets you as close as possible to hard data. A comparison with WHOIS data tells you how your threat intelligence systems work. To provide context on the performance of our threat intel feeds, we extracted WHOIS dates and found that almost all of the malicious trojan installer domains were blocked within 2 to 3 days after the WHOIS domain registration date. The WHOIS dates are relatively precise and provide another perspective on the high value and relative performance of DNS threat intel feed content.
The threat actors behind most campaigns have learned to continually create and change the domains they use to camouflage their malicious activities. New domains are issued every day. Any key domains used in perpetuating the malicious trojan installer campaign may be shut down at any time and replaced with new infrastructure. Infoblox DNS Early Threat Detection gives your cyber defenders an important advantage.
MITRE ATT&CK TACTICS AND TECHNIQUES USED BY THE MALICIOUS TROJAN INSTALLER FOR WINSCP AND PUTTY
| MITRE ATT&CK – Tactics and Techniques | ||
| Resource Development | ||
| Acquire Infrastructure: Malvertising | T1583.008: | The threat actor uses ads to promote malware delivery via popular search engines. |
| Initial Access | ||
| Drive-by Compromise | T1189: | The user clicks on a malicious ad populated from a typical search engine query for a software utility and is ultimately redirected to a page hosting malware. |
| Execution | ||
| Native API | T1106: | The malware dynamically resolves and executes functions from ntdll.dll at runtime. |
| User Execution: Malicious File | T1204.002: | The user downloads and executes setup.exe (renamed pythonw.exe), which side-loads and executes the malicious DLL python311.dll. |
| Command and Scripting Interpreter: Python | T1059.006: | The malware executes a python script to load and execute a Sliver beacon. |
| Persistence | ||
| Create or Modify System Process: Windows Service | T1543.003: | The threat actor creates a service to execute a C2 beacon. The threat actor loads a vulnerable driver to facilitate disabling antivirus software and other defenses present. |
| Scheduled Task/Job: Scheduled Task | T1053.005: | The threat actor creates a scheduled task to execute a C2 beacon. |
| Defense Evasion | ||
| Deobfuscate/Decode Files or Information | T1140: | The malware uses various string manipulation and obfuscation techniques. |
| File and Directory Permissions Modification: Windows File and Directory Permissions Modification | T1222.001: | The malware calls chmod to change file permissions prior to execution. |
| Hijack Execution Flow: DLL Search Order Hijacking | T1574.001: | The malware contained in python311.dll is loaded by a renamed copy of pythonw.exe from the same directory. |
| Hijack Execution Flow: DLL Side-Loading | T1574.002: | The malware contained in python311.dll is loaded by a renamed copy of pythonw.exe and proxies requests to a renamed copy of the legitimate DLL. |
| Obfuscated Files or Information: Software Packing | T1027.002: | The final payload executed by the malware is unpacked through several layers of compression, encryption, and file formats. |
| Obfuscated Files or Information: Encrypted/Encoded File | T1027.013: | The malware also stores other file dependencies with several layers of obfuscation |
| Process Injection: Dynamic-link Library Injection | T1055.001: | The malware loads a Sliver beacon DLL via python script. |
| Lateral Movement | ||
| Lateral Tool Transfer | T1570: | The threat actor uses SMB via Cobalt Strike to pivot post compromise |
| Exfiltration | ||
| Exfiltration Over Web Service: Exfiltration to Cloud Storage | T1567.002: | The threat actor attempts to exfiltrate data to a backup using Restic (a backup utility). |
| Impact | ||
| Data Encrypted for Impact | T1486: | The threat actor attempts the deployment of ransomware after exfiltrating data. |
Source: Ongoing Malvertising Campaign leads to Ransomware | Rapid7 Blog
Infoblox Threat Intel for Early Threat Detection
Infoblox Threat Intel uses proprietary techniques to identify potentially malicious domains much earlier than other technologies. Infoblox flags these domains as high risk so your defenders can automatically block them, often weeks to months before OSINT designates them malicious.
By taking this proactive approach, defenders can stop attacks days, weeks, or even months before they appear in OSINT or threat intelligence feeds.
Threat actors continually adjust their techniques and often use malicious domains to quickly launch damaging and dangerous attacks. Once that link to a malicious domain is clicked, the Kill Chain can rapidly unfold to the detriment of the defenders. These malicious domains are often detected and shared too late by OSINT and threat intel feeds
For Additional Information
Infoblox Threat Intel provides fast access to accurate, contextual threat alerts and reports from our real-time research teams. High-Risk Domains feeds were introduced as an Infoblox proprietary capability on November 10, 2022, and, since then, have successfully provided many thousands of customers with the advanced information to block domains that ultimately become malicious long before most other threat intelligence sources identify them as malicious. Infoblox allows your team to leverage the high value of DNS-based threat intelligence while ensuring a unified security policy across your entire security infrastructure. Infoblox threat data minimizes false positives, so you can be confident in what you are blocking.
| Infoblox Threat Intel data is HIGH VALUE, can be used with relatively LOW EFFORT, and can SHRINK THE TIME TO VALUE and INCREASE THE RETURN ON INVESTMENT for your threat intelligence program. |
To learn more about Infoblox Threat Intel and DNS early detection:
https://www.infoblox.com/threat-intel/
To learn more about BloxOne Threat Defense:
https://www.infoblox.com/products/bloxone-threat-defense/
OSINT sources on the Malicious Trojan Installers for WINSCP and PUTTY included, but were not limited to:
Ongoing Malvertising Campaign leads to Ransomware | Rapid7 Blog
To learn more about the National Security Agency (NSA) and Cybersecurity & Infrastructure Security Agency (CISA) guidance on Protective DNS:
https://media.defense.gov/2021/Mar/03/2002593055/-1/-1/0/CSI_PROTECTIVE%20DNS_UOO117652-21.PDF