Microsoft announced on Friday, May 2nd 2024, the private preview of a new Windows feature, Zero Trust DNS (ZTDNS) that aims to use a Zero Trust approach to IP-based traffic. This feature will lock down devices so that they can only access network destinations that are approved by a Protective DNS (PDNS) service. All other outbound IP traffic will be blocked except for connections to the Protective DNS servers and other required network connectivity services such as DHCP and NDP. There could be a small list of manual exceptions allowed for trusted IP subnets, to make sure certain services are accessible.
At Infoblox, we are strong supporters of Microsoft ZTDNS vision. Infoblox is the market’s best of breed provider for PDNS as well as enterprise owned DNS servers, and as such we can help any customer maximize the impact of adopting ZTDNS. From an industry point of view, we believe ZTDNS principles need to extend to other operating systems such as MacOS, iOS, Android, etc. as well and look forward to a time of wide adoption for ZTDNS.
What is Protective DNS?
Protective DNS (PDNS) is a security service that analyzes DNS queries and blocks resolution to malicious domains and IPs. Using a combination of DNS threat intelligence, AI/Machine Learning engine and Response Policy Zone (RPZ) functionality, PDNS prevents connections to known or suspected malicious sites including those that could be associated with ransomware, phishing, lookalike domains, data exfiltration and spyware, making the network inherently more secure.
Protective DNS server can disrupt the attack cycle at the first/initial step – at the intent to communicate – when a user or device tries to connect to a malicious destination. PDNS can decline to resolve that domain because it knows it is malicious. Instead, it can take the user to a walled garden site. All of this can be done before the other security devices such as NGFWs or proxies see this activity or can act on it. 92% of malware attacks can be blocked using DNS per the NSA, which means PDNS can stop threats earlier in the chain, help offload downstream security devices, and reduce alerts to the SIEM, sometimes as much as 50 to 60%. Government bodies across the world such as NCSC and CISA are making PDNS services available to agencies, ministries and emergency services to offer a layer of protection, and they strongly recommend the private sector to adopt PDNS as well.
Benefits of ZTDNS
While there may be some legitimate complications that will arise when ZTDNS is implemented, such as when using teleconferencing apps, media streaming and printing, as Microsoft rightly points out leveraging local network PDNS solution, such as Infoblox, can help mitigate many of these complications and provide a more complete and simpler to deploy solution. For those we can’t help with, the benefits still far outweigh any complications. By allowing connections to only those IP addresses resolved by the provisioned (and trusted) PDNS servers, enterprises using ZTDNS can:
- block bypassing of DNS when hard coded IP addresses are directly used
- prevent browsers from using not-trusted encrypted DNS resolvers, instead of using the approved operating system’s DNS
What this means from a business benefit perspective is that enterprises can now enforce DNS as an enterprise-wide security control point, proactively protecting devices from getting compromised and reducing risk to the business.
Infoblox PDNS and DNS Detection and Response
Microsoft ZTDNS is a validation of Infoblox’s long held position that DNS can be used for more than just domain resolution and is an amazingly effective security control. Providing true defense in depth and proactive security, DNS is a powerful tool to enforce security policy and protect the enterprise against cyberthreats. BloxOne Threat Defense from Infoblox is an industry leading Protective DNS server that provides comprehensive and earliest protection against cyberthreats such as ransomware, suspicious domains, phishing, spear phishing, lookalike domains, Zero Day DNSTM, DGAs and more.
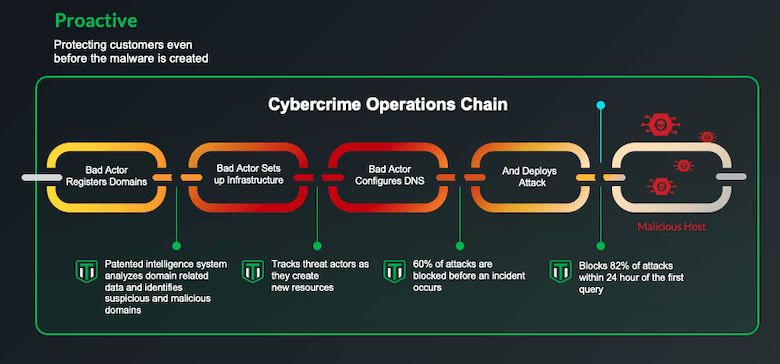
Infoblox Threat Intel tracks attacker infrastructure as it’s created, to identify both known and likely threats earlier. Through sophisticated algorithms, suspicious and malicious domains are detected even before those domains are weaponized and used in a malicious campaign. These detections are correlated and connected to threat actor infrastructure allowing Infoblox to keep tabs on the infrastructure as it grows and evolves. The threat intel is used in BloxOne Threat Defense for policy enforcement, stopping threats on an average 63 days before a domain has been used.
In addition to PDNS capabilities, DNS and related technologies such as IP Address Management and DHCP can be used to improve incident response capabilities as part of a comprehensive DNS Detection and Response solution. This involves:
- providing user and device attribution for security events to speed up triage, and
- integrating with the broader security ecosystem to automate downstream remediation actions.
Learn more about PDNS and BloxOne Threat Defense here.










